Today, we are going to try connectivity between two networks, connected by a multilayer switch.
We see two networks 172.16.0.0 (inside) and 5.0.0.0 (outside). Inside laptop with 172.16.0.10 and Outside laptop with 5.0.0.10. We check for ping between inside and outside laptops.
Task Breakup
Enable debugging at packet level
IP Routing information will be empty
Ping from Inside Laptop and Outside Laptop will not happen
4. Configuring routing on switch
Routing information will be populated with connected networks
5. Analysis after Routing
Issue ping from Inside laptop(172.16.0.10) to outside laptop(5.0.0.2) . It will be successful !!!
As packet debug is enabled, we will see the following dumps.
First 2 lines, indicates the routing process that happened for ICMP Echo Request packet with source IP(inside laptop) and destination IP (outside laptop)
Next 2 lines, indicates the routing process of ICMP Echo Reply packet with source IP (outside laptop) and destination IP(inside laptop)
 |
| Topology |
We see two networks 172.16.0.0 (inside) and 5.0.0.0 (outside). Inside laptop with 172.16.0.10 and Outside laptop with 5.0.0.10. We check for ping between inside and outside laptops.
Task Breakup
- Configuring IP address on Laptops
- Configure IP address on Switch
- Analysis before routing
- Configure routing on switch
- Analysis after routing
1. Configuring IP address on Laptop
Click on Laptop -> Desktop -> IP Configuration
 |
| Inside - Laptop - IP Configuration |
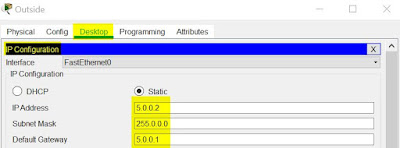 |
| Outside - Laptop - IP Configuration |
2. Configure IP addresses on Switch
As it is multilayer switch, we have to convert the interface into routing interface instead of switch interface. 'no switchport' is the command we use. We set the interface according to the details mentioned in Topology.
As it is multilayer switch, we have to convert the interface into routing interface instead of switch interface. 'no switchport' is the command we use. We set the interface according to the details mentioned in Topology.
routing#conf t Enter configuration commands, one per line. End with CNTL/Z. routing(config)#int gig 1/0/1 routing(config-if)#no switchport %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/1, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/1, changed state to up routing(config-if)#ip address 172.16.0.1 255.255.0.0 routing(config-if)#no shut routing(config-if)#exit
routing(config)#int gig 1/0/10 routing(config-if)#no switchport %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/10, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/10, changed state to up routing(config-if)#ip address 5.0.0.1 255.0.0.0 routing(config-if)#no shut routing(config-if)#exit
3. Analysis before Routing
Enable debugging at packet level
routing#debug ip packet Packet debugging is on routing#
IP Routing information will be empty
routing#show ip route Default gateway is not set Host Gateway Last Use Total Uses Interface ICMP redirect cache is empty
Ping from Inside Laptop and Outside Laptop will not happen
4. Configuring routing on switch
routing#conf t Enter configuration commands, one per line. End with CNTL/Z. routing(config)#ip routing routing(config)#exit routing#
Routing information will be populated with connected networks
routing#show ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
C 5.0.0.0/8 is directly connected, GigabitEthernet1/0/10
C 172.16.0.0/16 is directly connected, GigabitEthernet1/0/1
5. Analysis after Routing
Issue ping from Inside laptop(172.16.0.10) to outside laptop(5.0.0.2) . It will be successful !!!
As packet debug is enabled, we will see the following dumps.
IP: tableid=0, s=172.16.0.10 (GigabitEthernet1/0/1), d=5.0.0.2 (GigabitEthernet1/0/10), routed via RIB IP: s=172.16.0.10 (GigabitEthernet1/0/1), d=5.0.0.2 (GigabitEthernet1/0/10), g=5.0.0.2, len 128, forward IP: tableid=0, s=5.0.0.2 (GigabitEthernet1/0/10), d=172.16.0.10 (GigabitEthernet1/0/1), routed via RIB IP: s=5.0.0.2 (GigabitEthernet1/0/10), d=172.16.0.10 (GigabitEthernet1/0/1), g=172.16.0.10, len 128, forward
First 2 lines, indicates the routing process that happened for ICMP Echo Request packet with source IP(inside laptop) and destination IP (outside laptop)
Next 2 lines, indicates the routing process of ICMP Echo Reply packet with source IP (outside laptop) and destination IP(inside laptop)








